Become a Certified Data Protection Officer (CDPO)
CDPO is a practical certification by FCRF designed to equip professionals with the knowledge and tools needed to navigate India’s Digital Personal Data Protection Act (DPDPA) and global privacy laws like GDPR and CCPA. The course trains participants through real-world case studies, roleplays, and compliance simulations to become strategic privacy leaders in the digital age.

Live Classes By Expert
Renowned data protection officers, privacy-law practitioners, compliance leaders, and governance experts guide you through India’s Digital Personal Data Protection (DPDP) Act, 2023, global privacy frameworks (GDPR, ISO 27701), consent architecture, data-processing obligations, DPIAs, breach notifications, and privacy-by-design. You’ll gain clarity on how organizations operationalize compliance, manage data-handling risks, respond to regulatory directions, and navigate real-world challenges in privacy governance.
Data Protection Landscape
A dedicated track to help you understand data lifecycle management, consent frameworks, cross-border data transfers, vendor assessments, AI-driven risk models, privacy engineering, and breach-response workflows. You’ll explore case studies, simulations, and sector-specific privacy risks across fintech, health, government, and digital platforms—mirroring the evolving privacy and compliance ecosystem in India and globally.
Career-Defining Certification
Your opportunity to step confidently into roles such as Data Protection Officer, Privacy Manager, Compliance Lead, or Governance Specialist. The CDPO certification equips you with the competencies required to lead organizational compliance programs, design accountability frameworks, handle audits, and communicate effectively with regulators—building a career at the heart of India’s privacy-first digital future.
10th Jan, 2026
Starting Date
4 Weeks Duration
Sat & Sun, 3 PM
- 5 PM
Live Sessions
Recordings will be Provided
16 Modules
Curriculum

Snapshots from Our CCMP Program with CERT-In
Organised in collaboration with CERT-In, FCRF’s Certified Cyber Crisis Management Professional (CCMP) program was attended by over 500 top officials from civil services, defence, cybersecurity, and regulatory bodies. These glimpses capture our commitment to high-impact, nationally recognised training.
Learn Twice as Much: Live Classes + Full Access to Previous Expert Sessions
Participants of the CDPO program get exclusive access to all video lectures from FCRF’s first batch, featuring India’s foremost privacy, cyber law, and security practitioners. These recordings are available on the FCRF LMS from Day 1—ensuring every learner gains comprehensive guidance in addition to the ongoing live weekend sessions.
India Needs Data Protection Leaders - Will You Be One?
✅ Master the Digital Personal Data Protection Act (DPDPA)
✅ Understand GDPR, CCPA & Global Privacy Frameworks
✅ Implement Consent Management & Transparency Tools
✅ Build Data Maps, RoPA & Retention Schedules
✅ Manage DSARs, Right to Erasure & User Access
✅ Conduct DPIAs, Vendor Assessments & TIAs
✅ Prepare for Data Breach Response & Notifications
✅ Navigate Cross-Border Data Transfers & Compliance
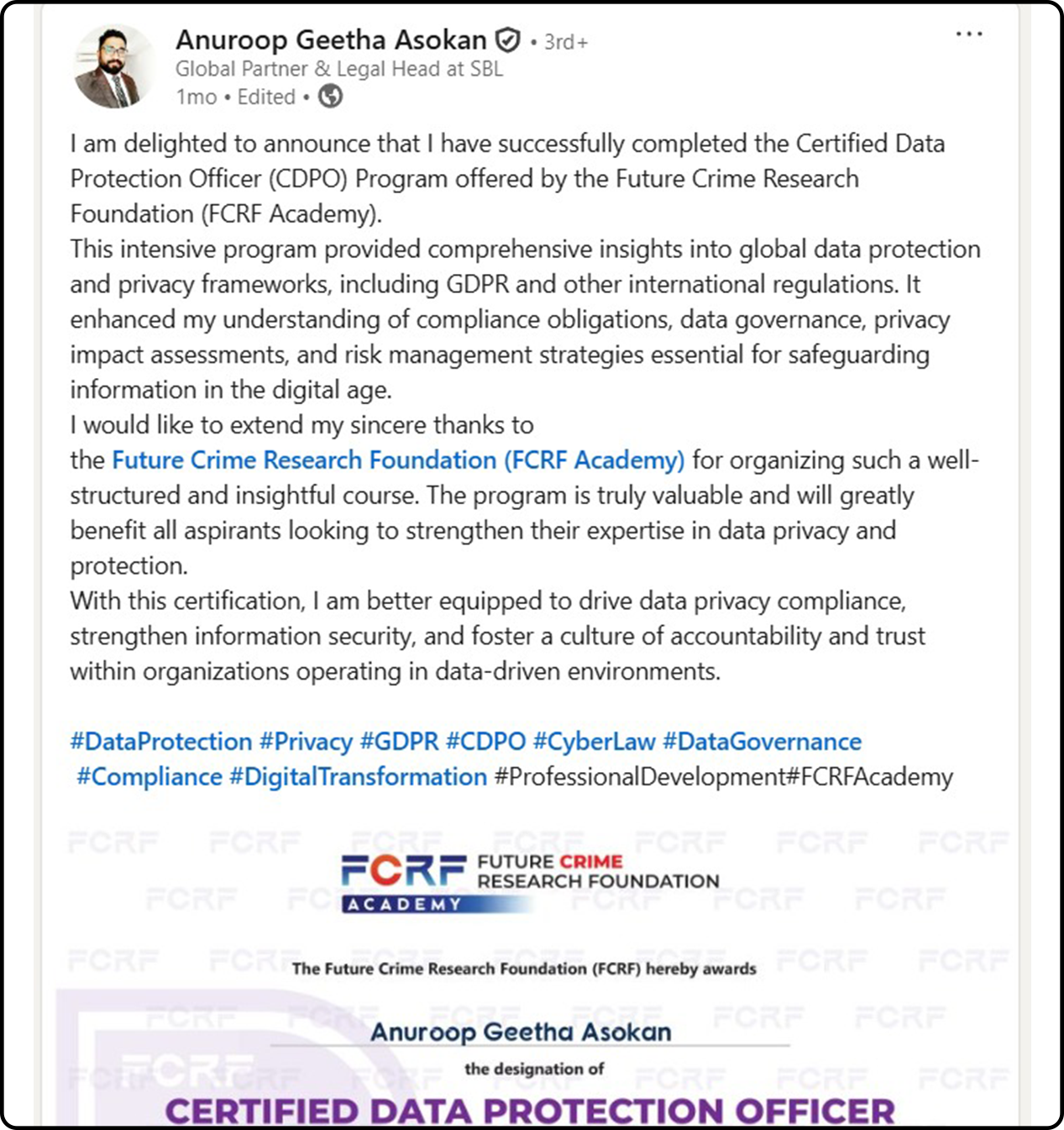
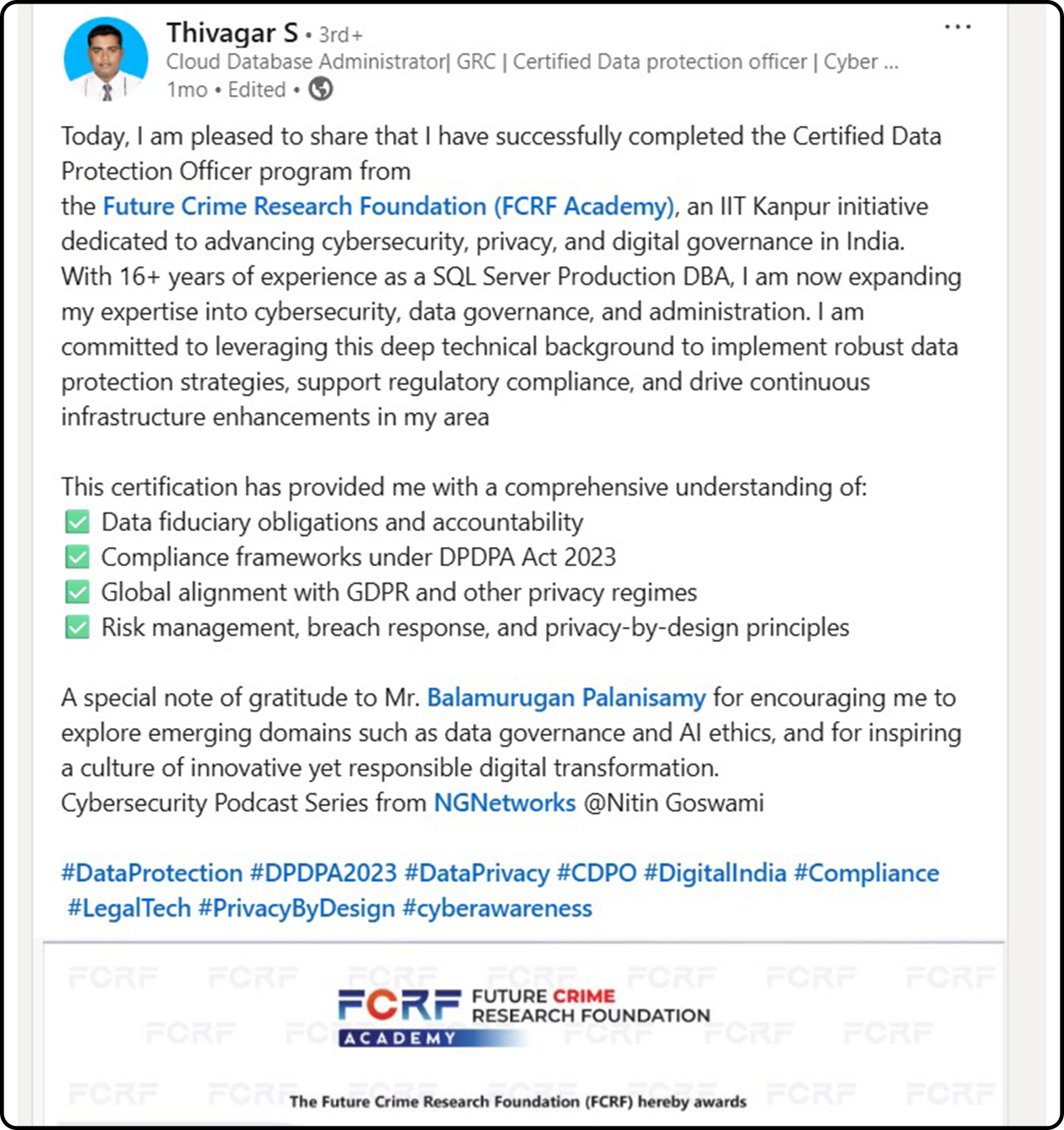
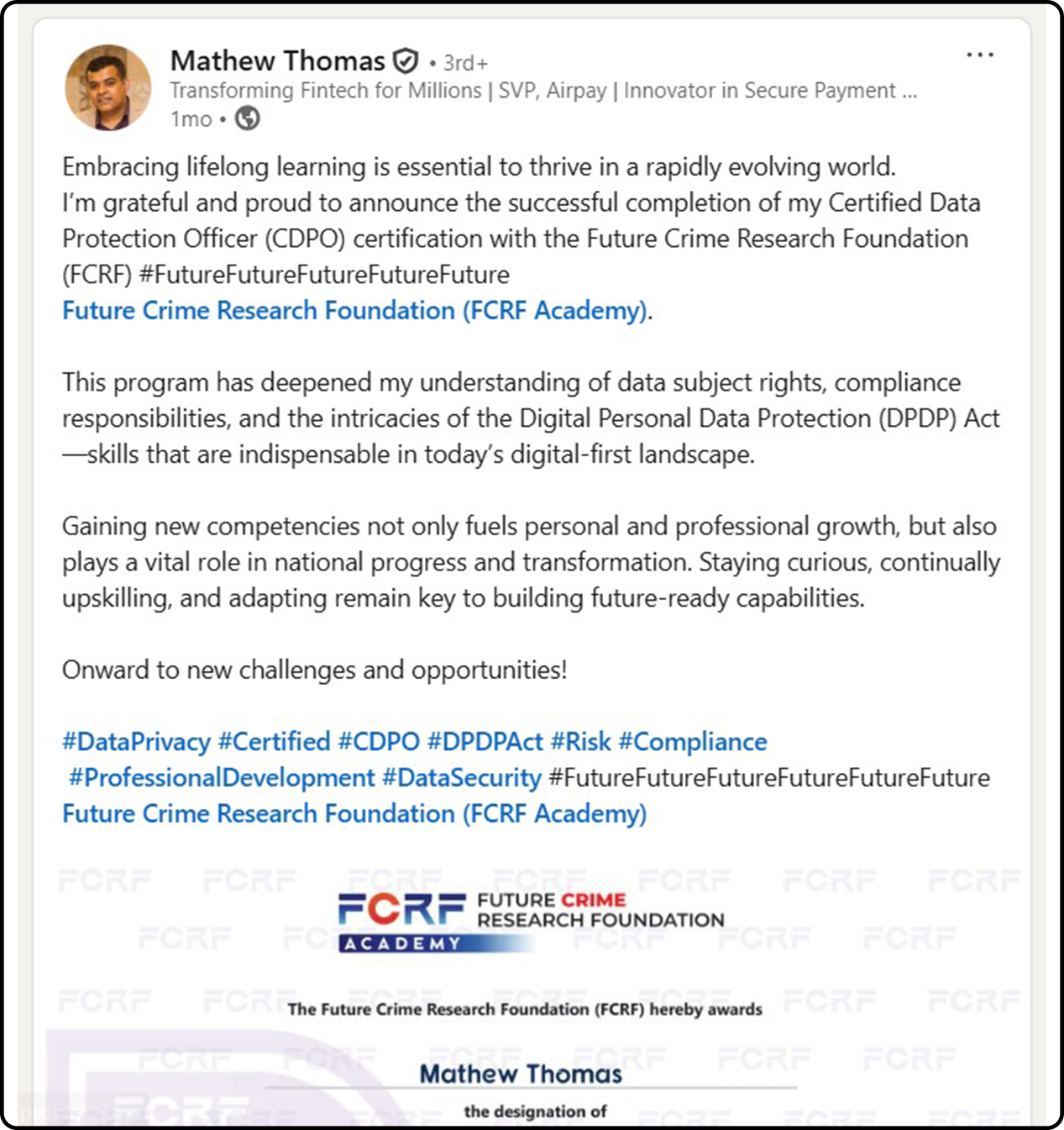
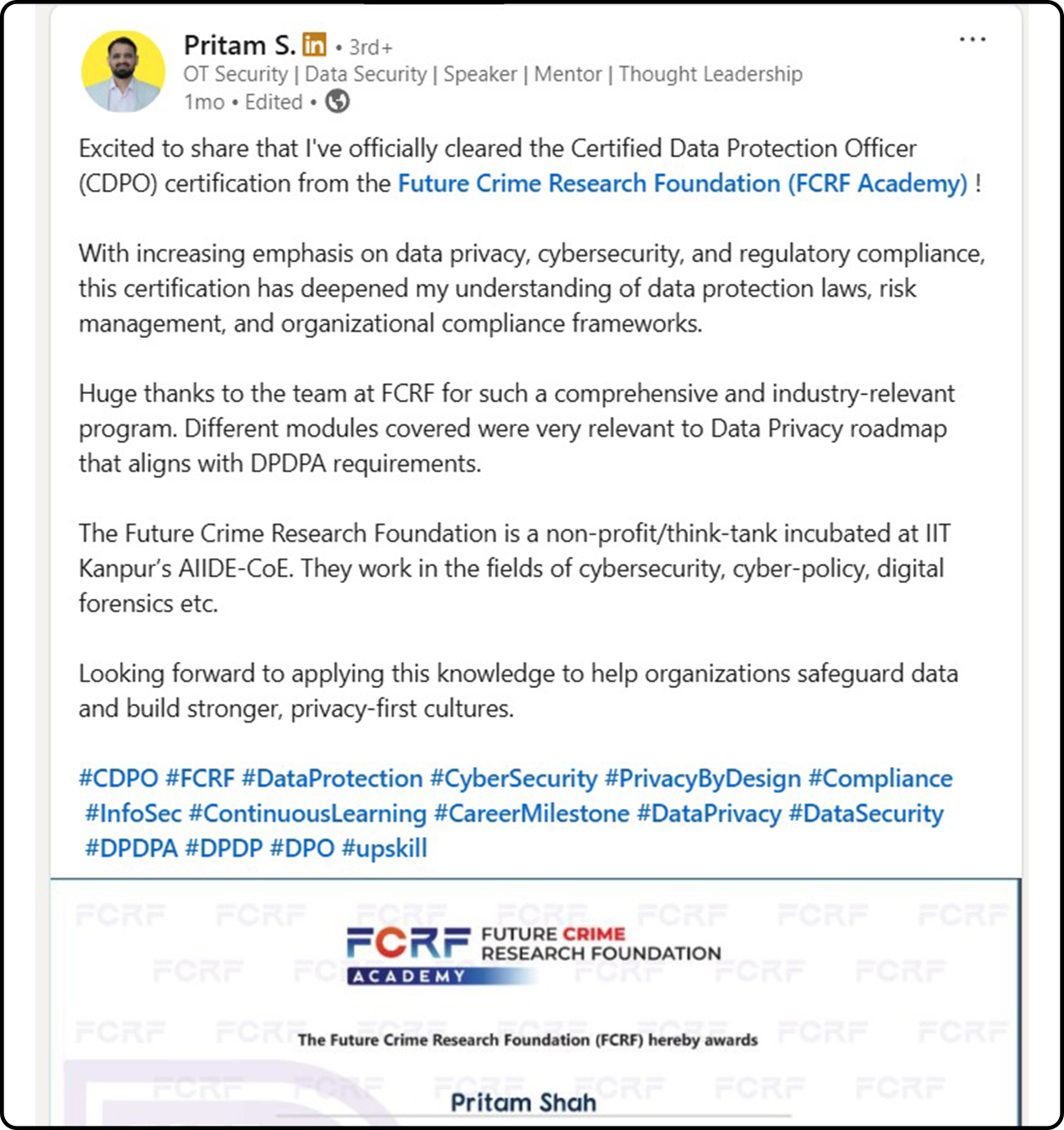
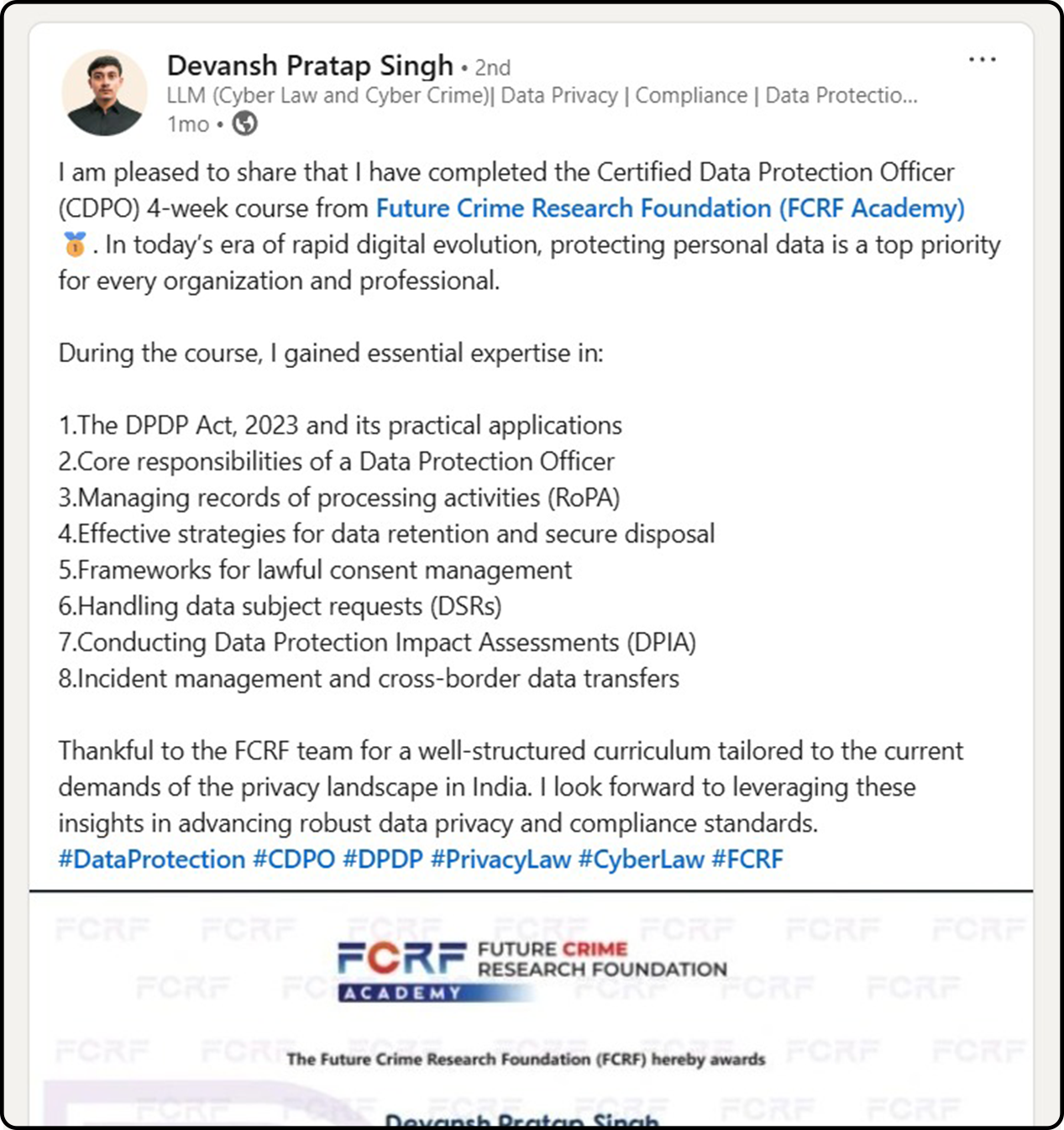
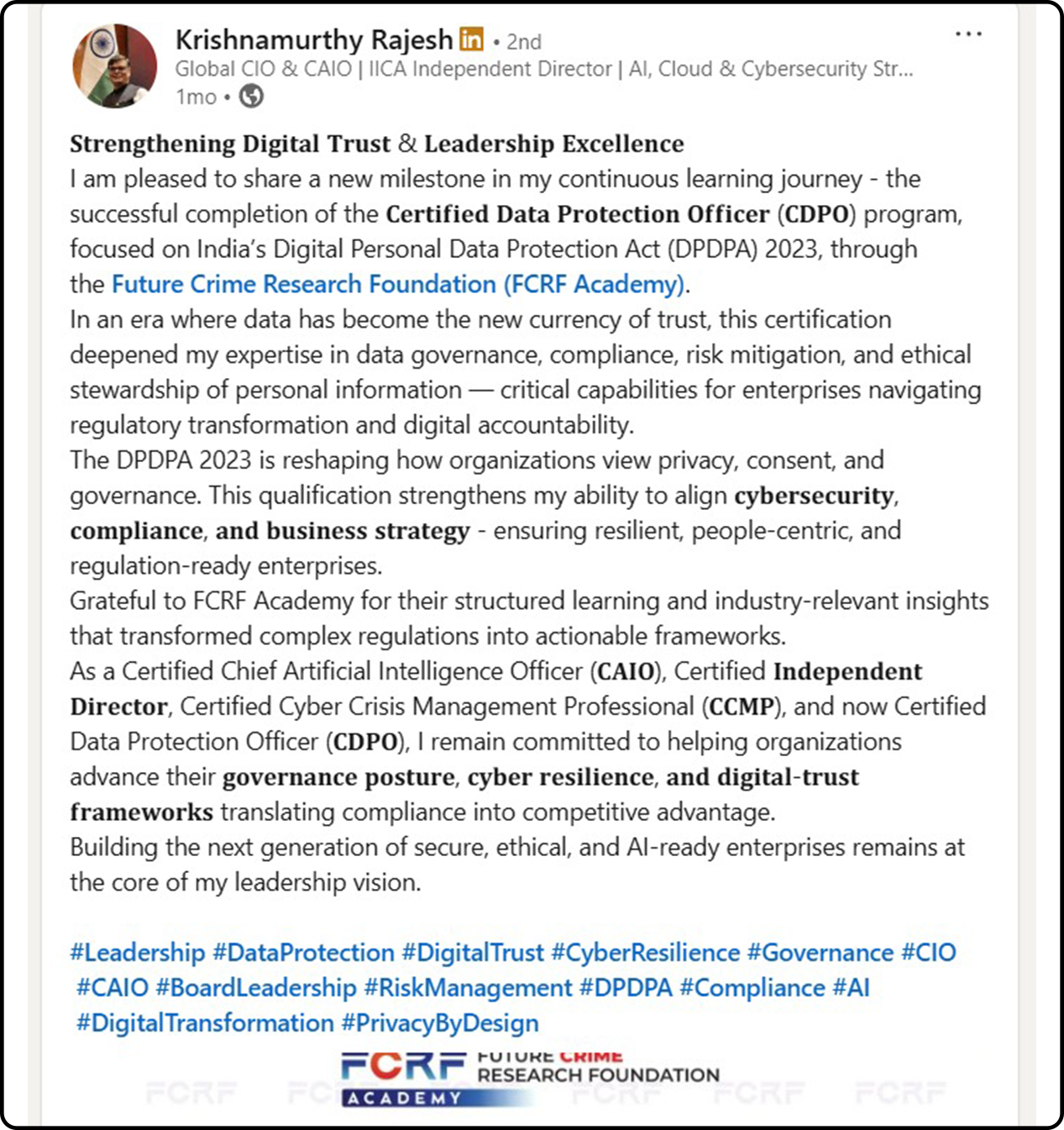
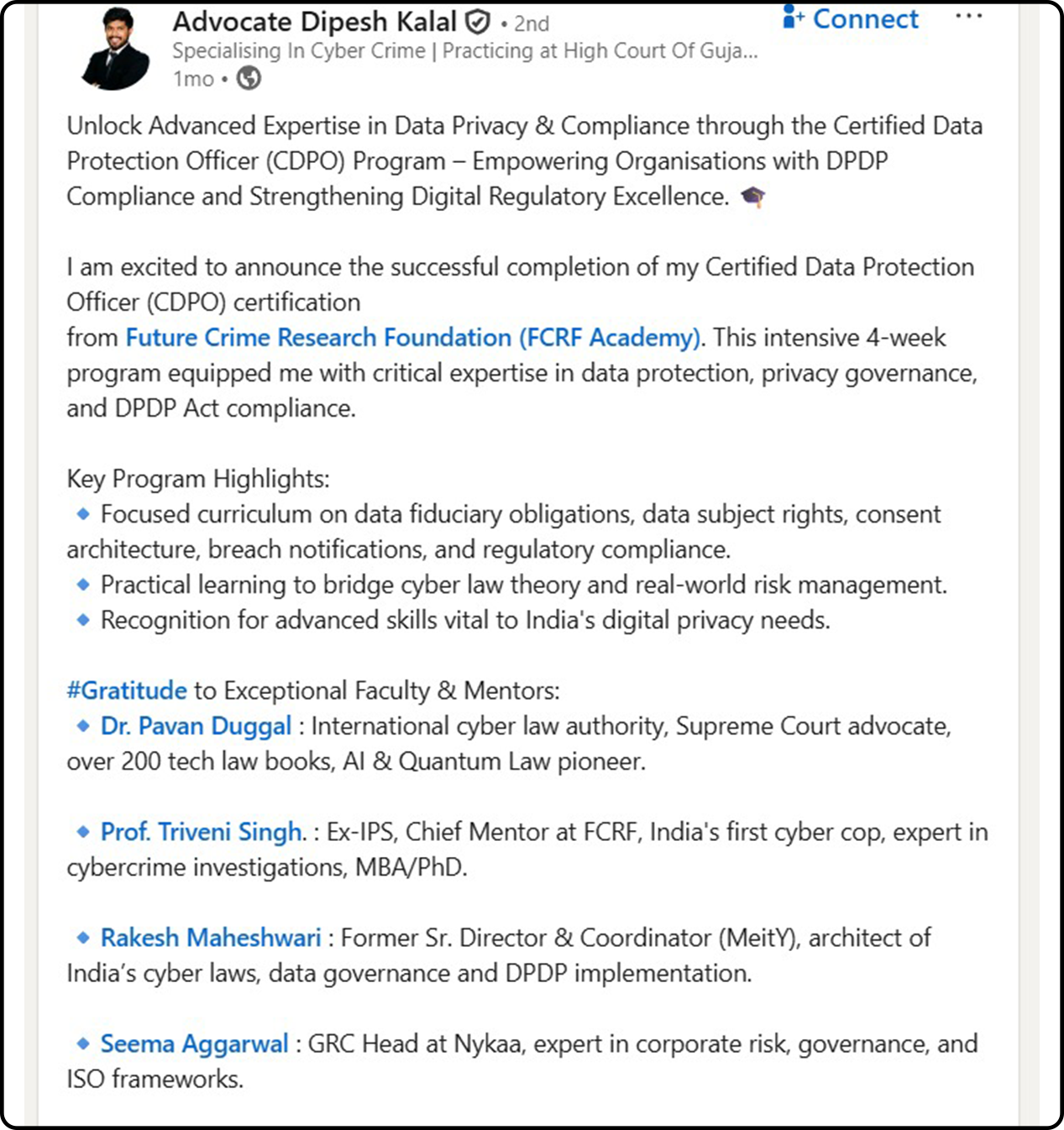
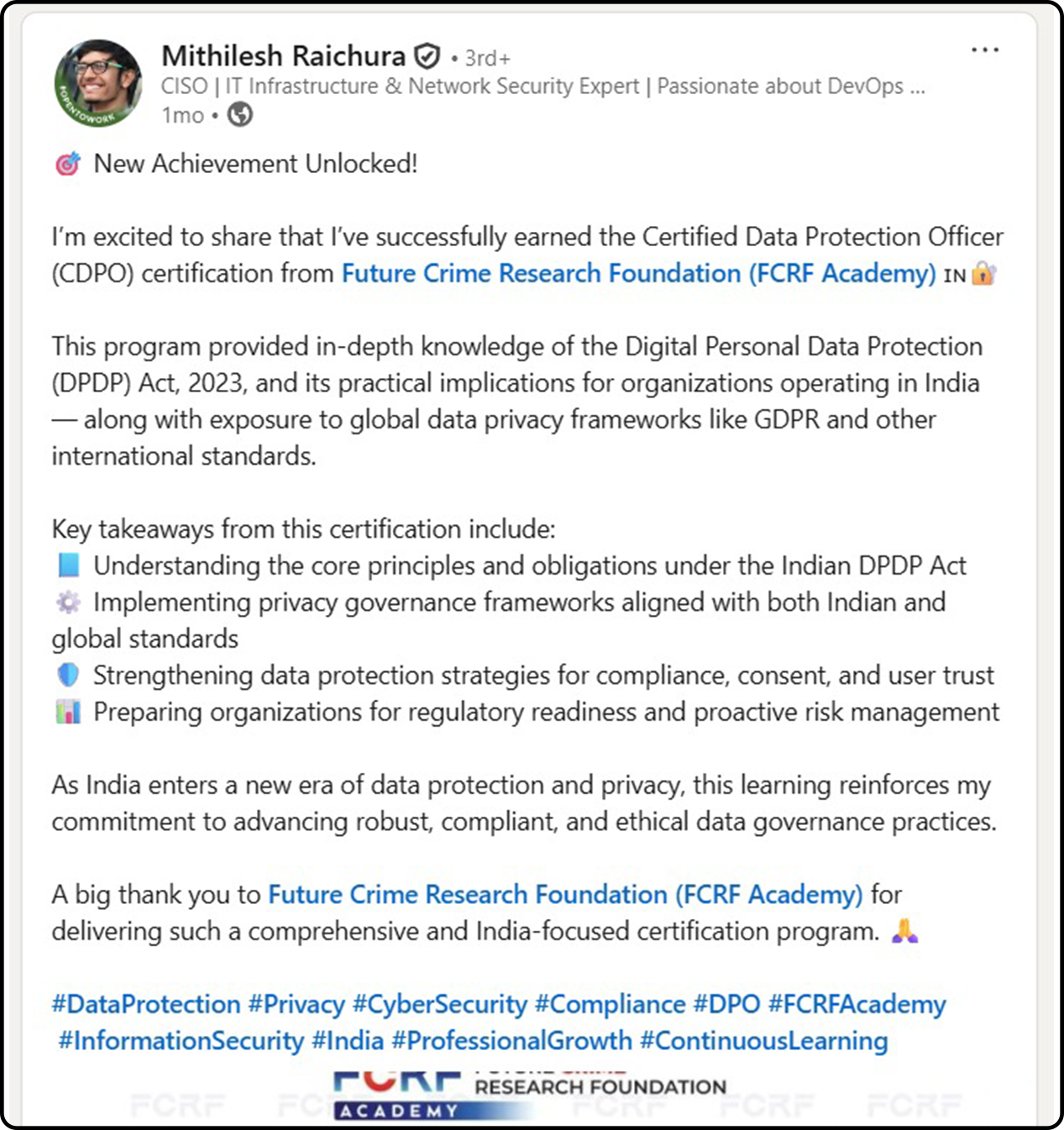
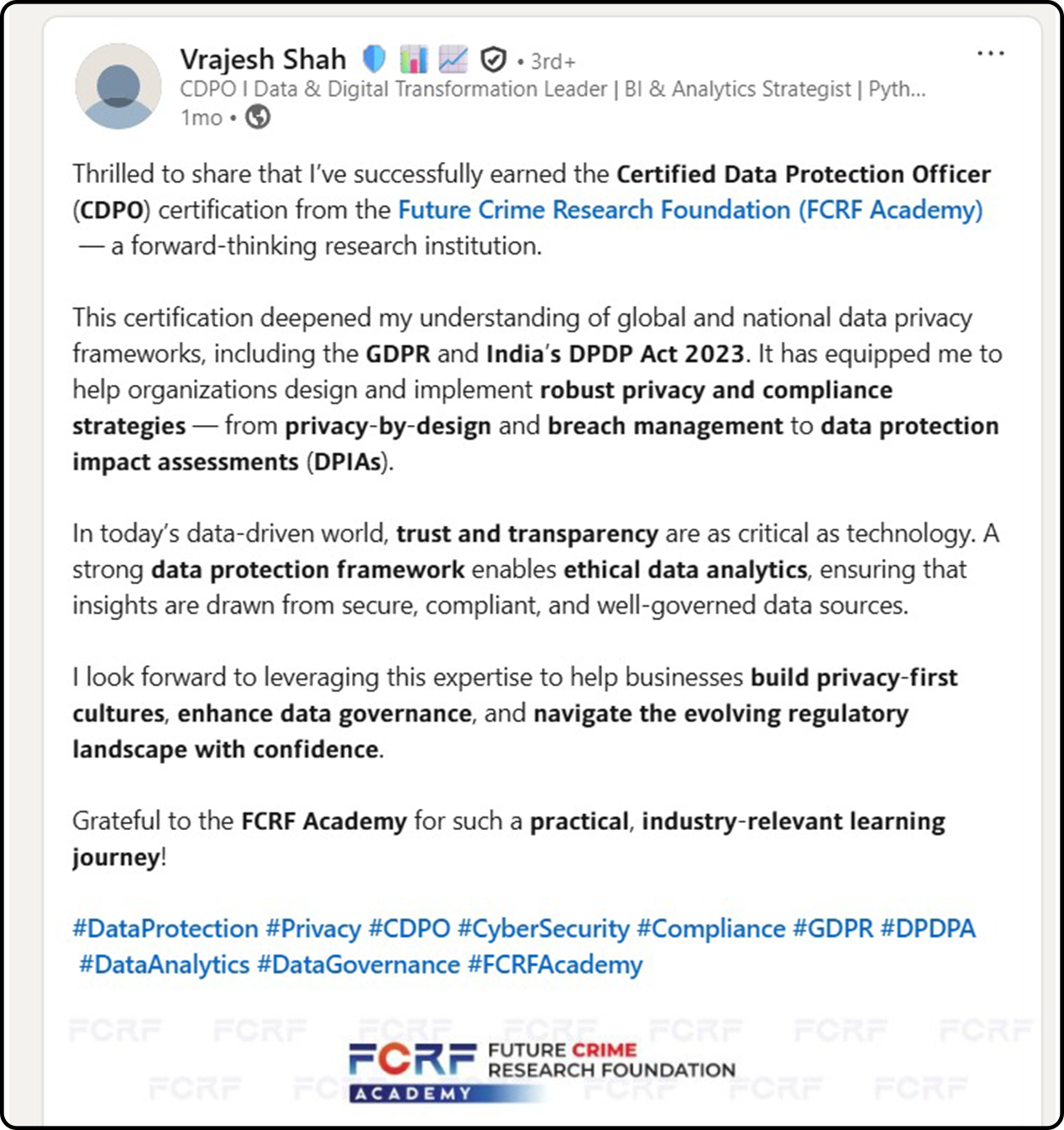
Hundreds of India’s Privacy Leaders Trust FCRF’s CDPO Certification
From CISOs and GRC experts to civil servants and compliance managers, professionals across sectors have successfully completed FCRF’s Certified Data Protection Officer (CDPO) program. The certification has empowered them with practical, India-focused expertise in DPDPA compliance, data governance, breach management, vendor risk, and global privacy frameworks—giving them a significant edge in the fast-evolving landscape of data protection.
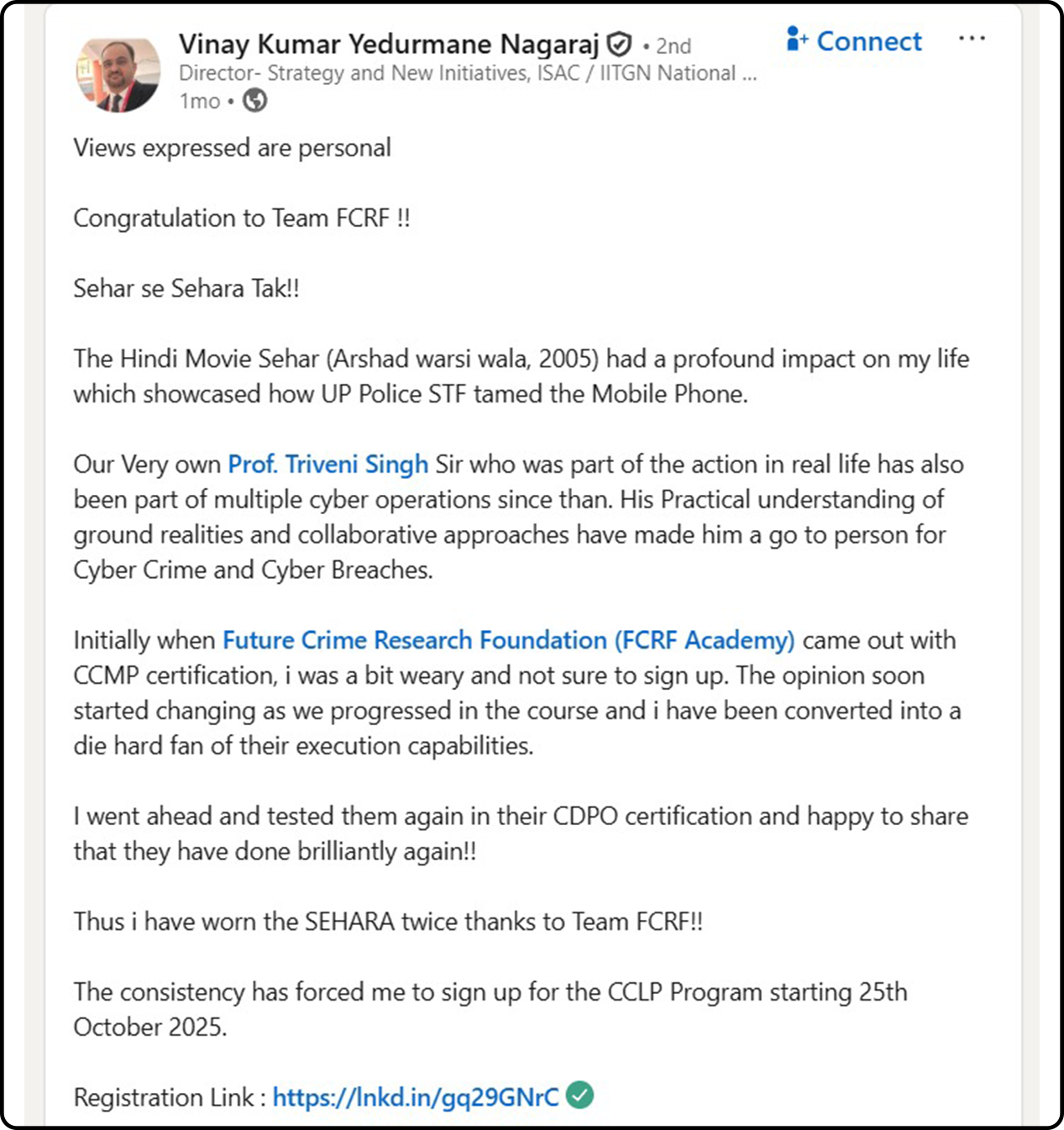
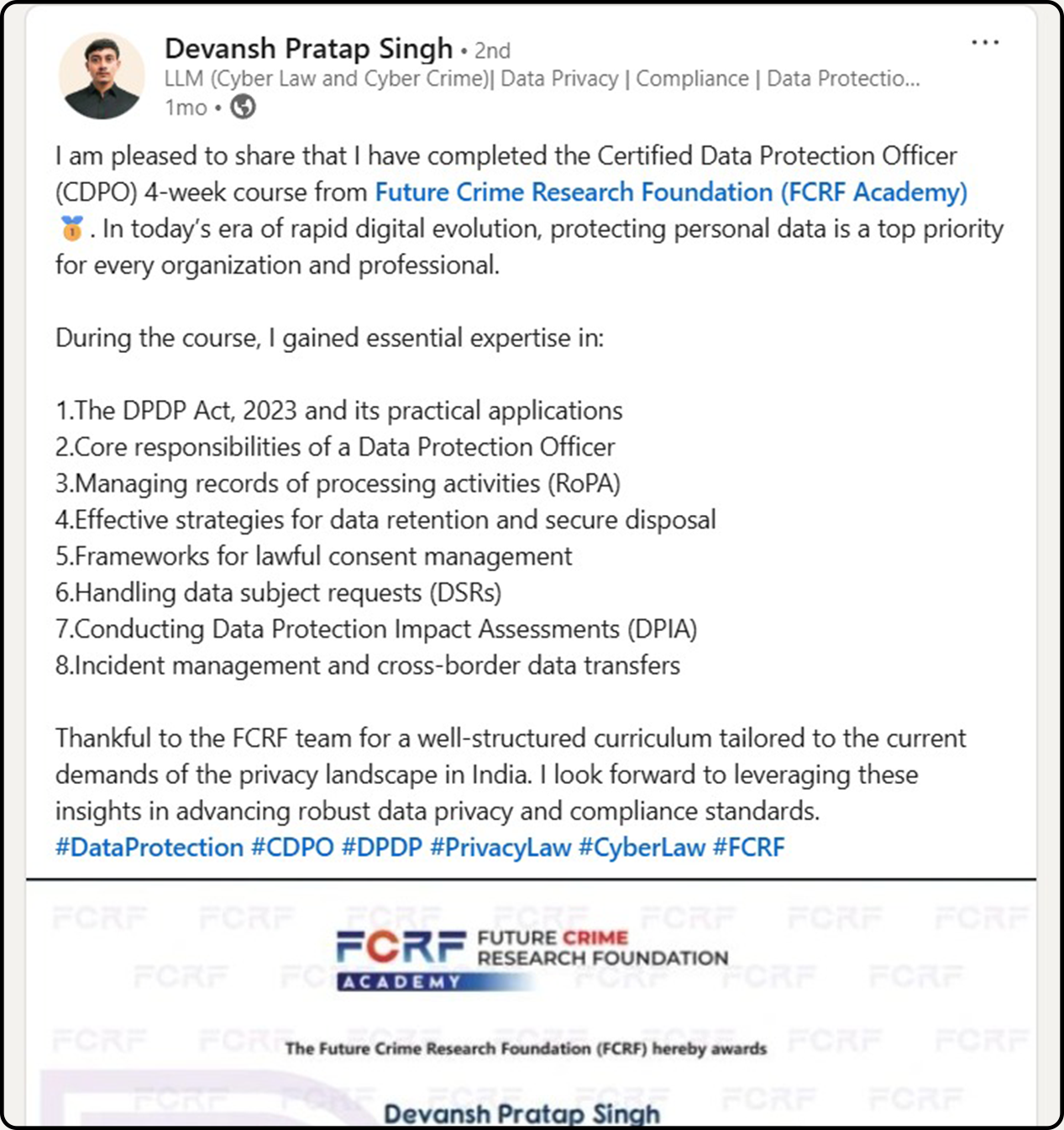
Discover Why CDPO is The Perfect Starting Point
A beginner-friendly, expert-crafted program to help you master data privacy regulations and launch a career in data protection and compliance leadership.
- 16 Modules aligned with India’s DPDPA and global privacy frameworks (GDPR, CCPA).
- Learn key domains like consent, DSARs, DPIAs, RoPA, breach notification & vendor risk.
- Privacy Governance Foundations to help you step into your first role as a certified Data Protection Officer.
- Designed to address real-world use cases and compliance needs across sectors.
- Exercises, templates, and roleplays across legal, tech, and managerial privacy functions.
- Now is the best time to become a Certified Data Protection Officer with India’s new data law in force.
Who Can Join The CDPO Program?
Open to professionals, learners, and leaders across IT, legal, governance, and compliance domains—especially those preparing for roles in data protection, privacy, and regulatory functions.
Course Module
Comprehensive, industry-aligned modules covering core data protection principles, practical compliance workflows, and real-world case studies from India’s DPDP Act, global privacy regulations, and enterprise privacy operations—designed to build strong, job-ready data protection expertise.
Introduction to Global Data Protection
- History and evolution of privacy as a right.
- Overview of major global privacy laws (e.g., GDPR, CCPA).
- Core definitions: Personal Data, PII (Personally Identifiable Information), Sensitive Personal Data, Processing, Data Controller, Data Processor.
- Identifying key privacy stakeholders within an organization and the regulatory landscape.
Deep Dive into the Digital Personal Data Protection Act (DPDPA)
- History and legislative journey of the DPDPA.
- Applicability: Territorial and material scope.
- The 7 Principles of Data Protection under DPDPA.
- Grounds for lawful processing.
- Significant Data Fiduciaries (SDFs): Criteria and additional obligations.
Establishing a Data Privacy Governance Framework
- GRC (Governance, Risk, and Compliance) principles.
- Developing a data privacy vision, mission, and strategy.
- Creating a comprehensive Data Privacy Governance Framework.
- Data Risk management strategies.
- Drafting and implementing key documentation: Data Protection Policy, Privacy Notice, etc.
- The concept of Privacy by Design and Default.
- Introduction to Privacy Enhancing Tools (PETs).
The Role & Responsibilities of the Data Protection Officer (DPO)
- The DPO’s role as per DPDPA and GDPR.
- Key responsibilities: monitoring compliance, advising on DPIAs, acting as a contact point.
- Reporting structures: Reporting to the highest level of management/board.
- Essential skills: Legal, IT, risk management, and communication.
- Managing Legal & Regulatory Risk.
- Collaboration with other functions (Legal, IT, InfoSec, HR, Marketing).
Data Mapping and Discovery
- Data discovery methodologies (questionnaires, interviews, automated tools).
- Creating and maintaining an inventory of personal data assets.
- Understanding data lifecycles from collection to deletion.
Data Flow Diagramming (DFD).
Records of Processing Activities (RoPA)
- Legal requirements for maintaining RoPA under DPDPA and GDPR.
- Mandatory fields and essential information to include.
- Using RoPA as a foundation for risk assessments and demonstrating accountability.
- Process for regular review and updates.
Data Retention, Archival, and Secure Disposal
- Principles of data minimization and storage limitation.
- Defining and documenting data retention schedules for different data types.
- Procedures for secure data archival.
- Methods for secure data disposal and deletion (e.g., wiping, degaussing, physical destruction).
- Understanding the “Erasure of Personal Data” timeline (as per DPDP Rules).
The Principles of Lawful Consent Management
- The definition of valid consent: Free, specific, informed, unambiguous, and clear affirmative action.
- The form and content of a valid notice.
- The right to withdraw consent and the ease of withdrawal.
- Consent vs. Deemed Consent: Understanding the difference.
Consent Managers and Technical Implementation
- The role of the “Consent Manager” under the DPDPA.
- User experience design for consent interfaces.
- Technical implementation: Consent Management Platforms (CMPs).
- Recording, tracking, and managing consent and withdrawal records.
Special Categories: Children's Data & Cookie Management
- Specific rules for processing children’s personal data.
- Obtaining verifiable parental/guardian consent.
- Cookie types (essential, functional, marketing) and their legal implications.
- Drafting a compliant Cookie Policy and implementing a cookie banner.
- Conducting a cookie audit and reporting.
Managing Data Subject Rights (DSRs)
- Overview of Data Subject Rights under DPDPA (Right to Access, Correction, Erasure, etc.).
- Building a DSAR intake, verification, and fulfillment workflow.
- eDiscovery considerations in DSAR fulfillment.
- Grounds for refusing a request (derogations).
- Timelines and requirements for responding to requests.
- Maintaining a DSAR log.
Data Protection Impact Assessments (DPIA)
- Difference between a PIA and a DPIA.
- Triggers: When is a DPIA mandatory?
- The DPIA process: Describing the processing, assessing necessity, identifying and mitigating risks.
- Assessing risks of new technologies (e.g., AI & Privacy).
- Consulting with the DPO and, if necessary, the Data Protection Board.
- Periodic review of DPIAs.
Cross-Border Data Transfer
- Restrictions on international data transfers.
- Concept of “adequacy” and the government’s role in specifying permitted countries.
- Legal transfer mechanisms: Standard Contractual Clauses (SCCs), Binding Corporate Rules (BCRs), explicit consent.
- Conducting Transfer Impact Assessments (TIAs)
Data Breach Incident Management
- Differentiating between a security incident and a data breach.
- Understanding threat vectors (OSINT, Synthetic Identity).
- Data Breach & Dark Web
- DFIR (Digital Forensics and Incident Response)
- The four phases of incident response: Preparation, Detection & Analysis, Containment & Eradication, Post-Incident Activity.
- Business Continuity & Disaster Recovery (BCP/DR)
Data Breach Notification and Communication
- Mandatory breach notification requirements under DPDPA.
- Timelines for notification (e.g., “without delay,” “72 hours”).
- Information to be included in the notification to the Data Protection Board and affected individuals.
- Maintaining a data breach register.
- Communication strategies to manage reputational damage.
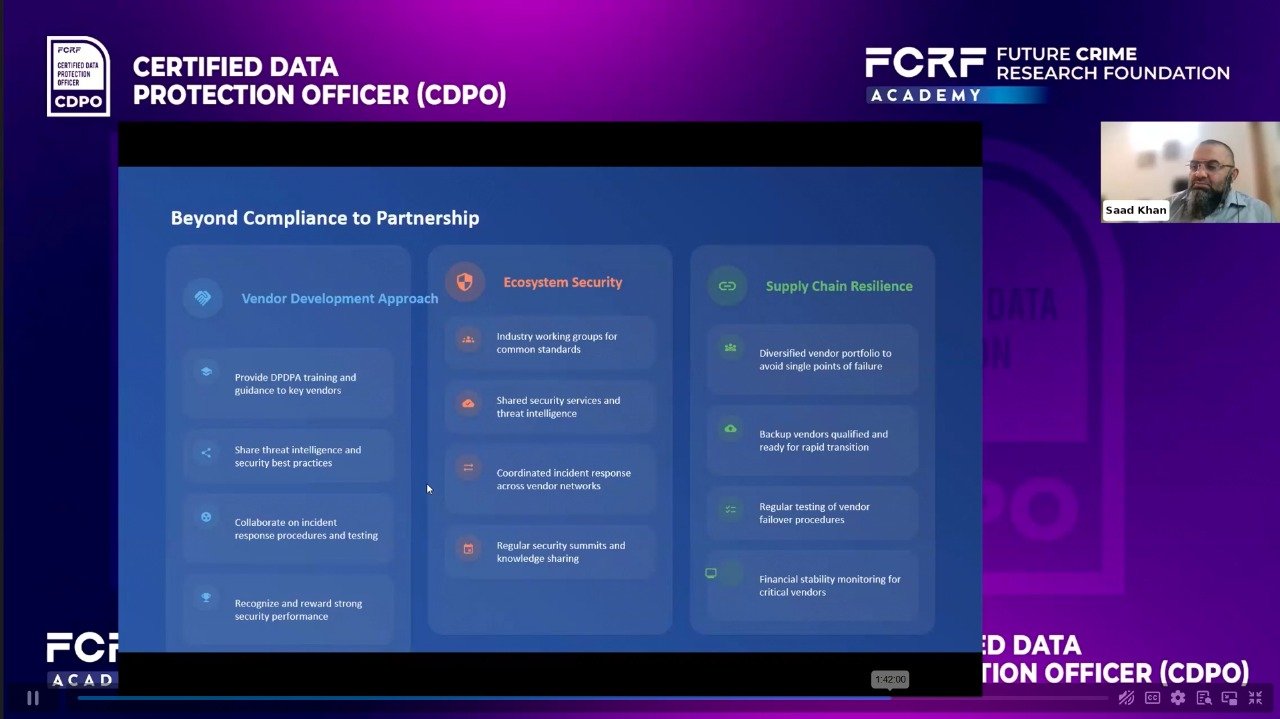
Vendor Management & Future Strategies
- The legal distinction and responsibilities of Data Fiduciaries and Data Processors.
- Vendor due diligence and risk assessment processes.
- Drafting and negotiating Data Processing Agreements (DPAs).
- Ongoing monitoring and auditing of data processors.
- Future Strategy for Compliance Professionals.
Newly Released DPDP Rules
Key operational rules on notice, consent, withdrawal, and grievance timelines.
Updated compliance duties for Data Fiduciaries and Data Processors.
Standardised procedures for Data Principal rights such as access, correction, and erasure.
Additional obligations for Significant Data Fiduciaries (SDFs), including audits and DPIA requirements.
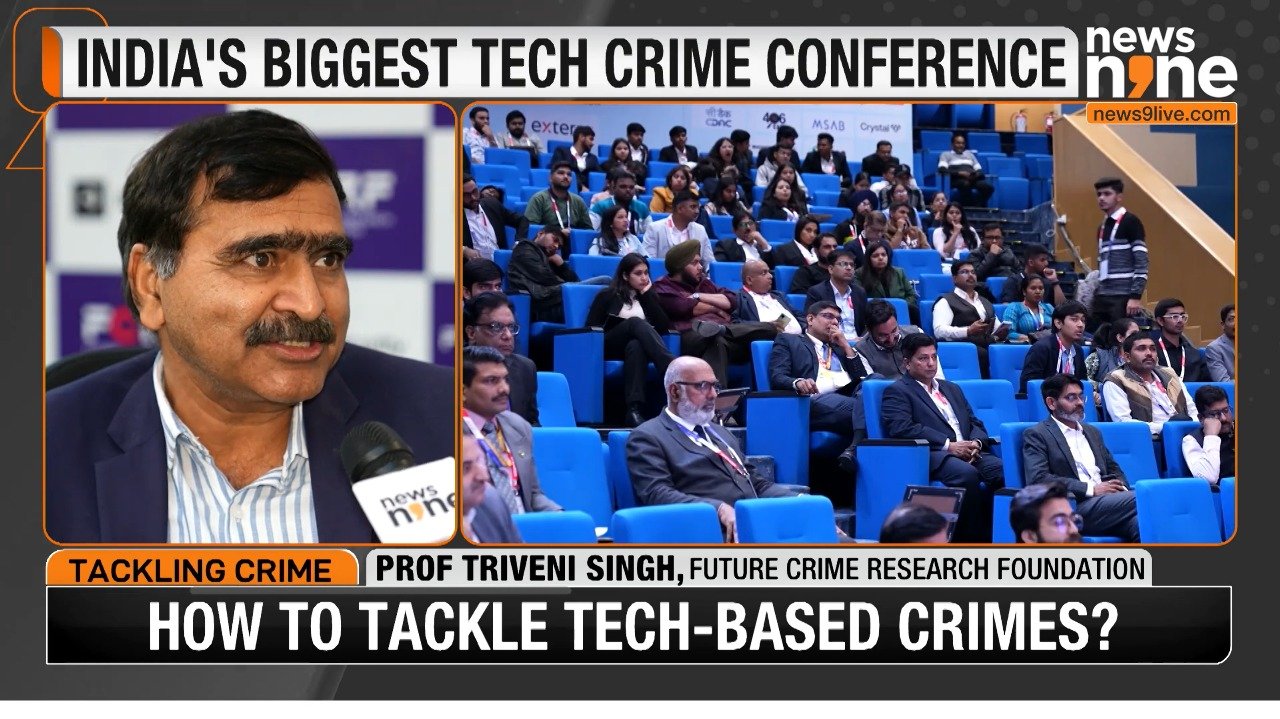

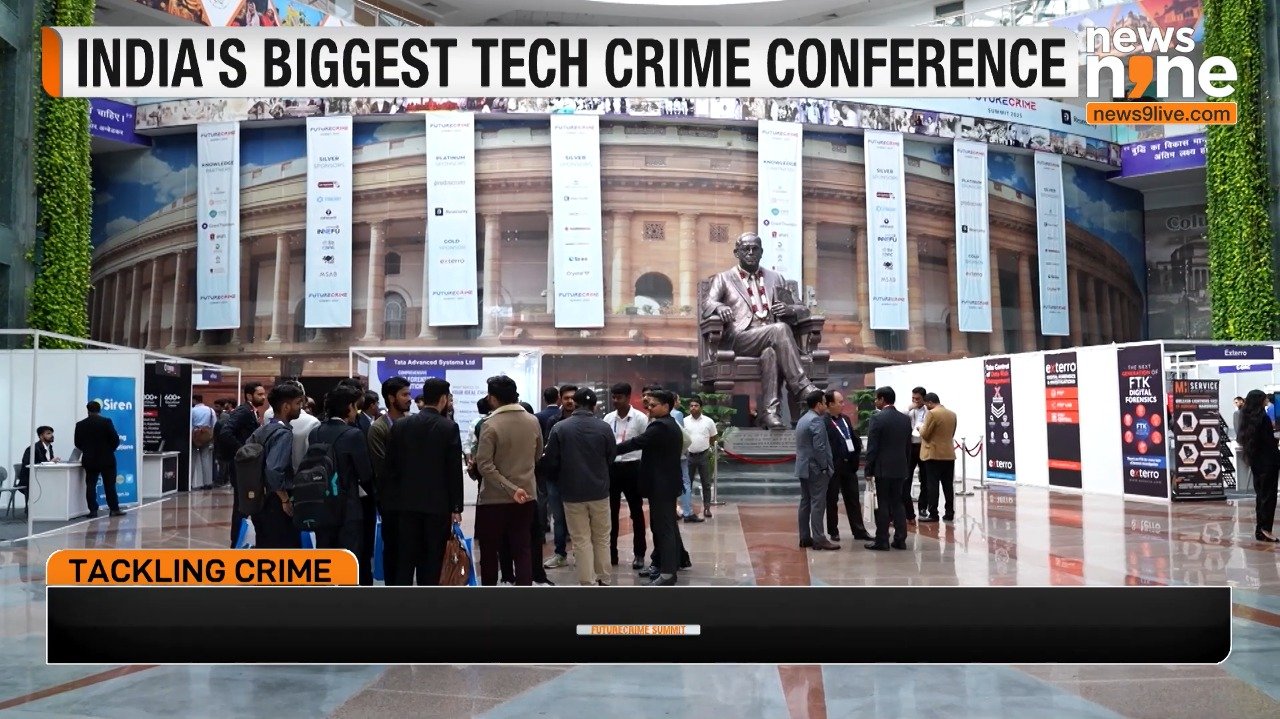
FCRF's Pioneering Role In Ensuring A Cyber-Safe India
Future Crime Research Foundation (FCRF) is an IIT Kanpur’s AIIIDE–CoE incubated start-up (Non-Profit NGO) specializing in research in Cyber Security, Digital Crime, Fraud Risk Management, Cyber Laws, and Cyber Forensics. FCRF is also the host of India’s largest conference on tech-enabled crime and cyber threats, the FutureCrime Summit. It is registered under Section 8 of the Companies Act, 2013, and Sections 12A and 80G of the Income Tax Act, 1961. FCRF strives to make India future-ready by increasing digital awareness and building an ecosystem for a cyber-safe India.
Join the program . Gain the certification . Lead in privacy .

FCRF’s Esteemed Speakers at the FutureCrime Summit





What Our Learners Say About Us
From senior officers to first-time professionals, our participants consistently praise the real-world relevance, expert-led delivery, and practical focus of our programs.
Well-organised sessions, very good speakers, and nicely structured content.
Well-structured and not too heavy, perfect for working professionals.
Content planning, pace of course. From scratch, so that all are on the same platform.
Informative sessions delivered with clarity and precision.
What I liked most about the CCMP Cyber Crisis course was how it explained tough topics in a simple way using real-life examples.
Case studies and introduction to professionals who could articulate towards today's situation.
All the speakers in the course are from very well reputed organisation having deep understanding in cybersecurity, really learnt a lot.
The course was well organised, and lecture by the industry experts was superb, Covered advanced topics like XDR, SIEM, and threat intelligence in depth.
Group Enrollments & Institutional Payments
We offer exclusive group discounts for departments, organisations, and corporate teams. Participants can also be manually enrolled on behalf of their organisation, with a consolidated invoice issued for institutional payment.
To avail group access or inquire further, Contact Us:
Have any questions? Find answers here!
Find answers to common questions below. For more queries, contact: research@futurecrime.org
Should I use my laptop, tablet, or phone to access this course?
While the course is accessible on all devices, we recommend using a laptop for the best learning experience—especially for live sessions, practical labs, and assignments. However, the FCRF Academy app will also be available on the App Store and Google Play Store by mid-June, allowing you to learn on the go with your phone or tablet.
What is the total duration of the course?
The course runs for 4 weeks, with live sessions every Saturday and Sunday from 3:00 PM to 5:00 PM IST.
Will this be live or pre-recorded?
The course is conducted live by expert instructors, with recordings made available after each session for revision and convenience.
I made the payment but didn’t receive any email
If you’ve made the payment but haven’t received confirmation, please check your spam folder. If not found, email us at research@futurecrime.org with your payment details.
Are the sessions interactive? Can I ask questions?
Absolutely. All sessions are live and interactive, and learners are encouraged to ask questions during and after class.
Is a refund available after payment and registration?
Kindly go through the syllabus and curriculum of the course carefully. No refund is possible once the payment is made. Though, we highly recommend all to enroll in this program.
Will I get lifetime access to course content?
You’ll receive lifetime access to session recordings, downloadable resources, and reading materials provided during the course.
Will I be added to a WhatsApp or Telegram group?
Yes, you’ll be added to the official CDPO WhatsApp group for updates, resources, and peer discussions. We’ll send the invite link via email and WhatsApp after registration.
If you don’t receive it, feel free to reach out at research@futurecrime.org.